

How often do you think about the privacy of your internet connections? With global losses from cybercrime exceeding $6 trillion in 2021 and projected to surpass $10.5 trillion annually by 2025, online security has never been more crucial! This article guides you in understanding proxy servers and how they offer a valuable means of enhancing online security for both individuals and businesses. Let's explore how they work and their key benefits.
Proxy Server Basics
What is a proxy server?
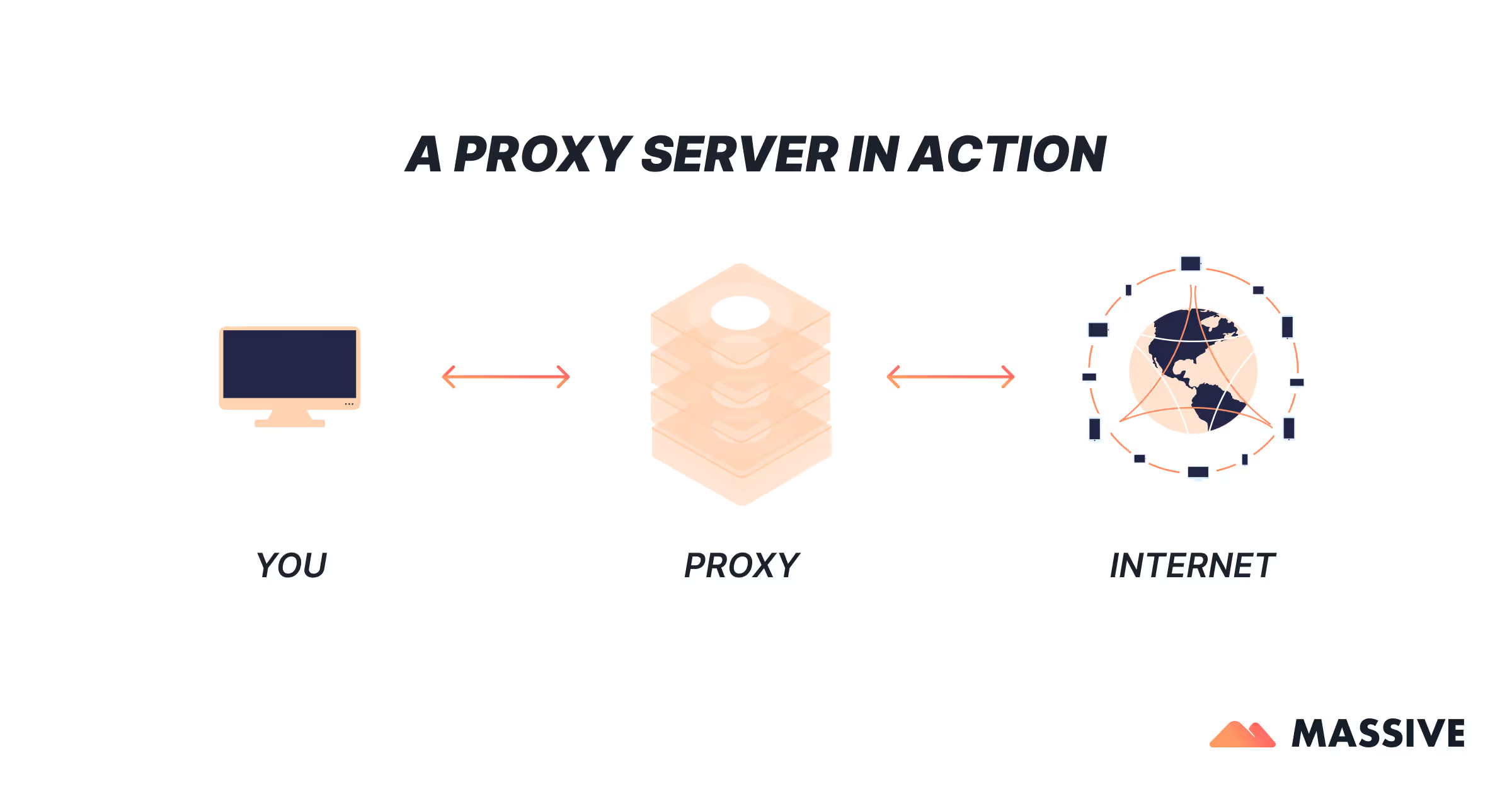
A proxy server is a server that sits between users and the internet, acting as a “proxy” for their traffic. To route their requests through a proxy server, users need to connect to a specific proxy server address (IP address and port). It adds one degree of separation between users and the site or service they want to connect with. This separation helps to mask the user’s IP address, providing a layer of privacy and security.
How does a proxy server work?
A proxy server acts as an intermediary server separating different networks or services. It forwards web requests and data received from websites, providing varying levels of functionality, security, and privacy. A proxy server works by routing connection requests through the proxy server to the website’s server, and it establishes and maintains connections between the user and the web server. This is how a proxy server work in managing and routing internet traffic.
Types of Proxy Servers
Forward Proxy Server
A forward proxy server is the most common type of proxy, forwarding your information request to the proxy server, passing it through a firewall, and sending it to the intended domain. Forward proxies are typically used for caching, anonymity, and content filtering. They are widely used in corporate networks to control and monitor employee internet usage. By caching frequently accessed web content, forward proxies can also help improve network performance and reduce bandwidth costs.
Reverse Proxy Server
A reverse proxy server, also known as a surrogate proxy, works in the opposite direction as a forward proxy, passing requests from the internet to users in an internal network. Reverse proxies are used to enhance security, load balancing, and to distribute traffic among multiple servers to ensure availability and reliability. They can protect internal servers from direct exposure to the internet, reducing the risk of attacks and ensuring that the load on any single server is minimized.
Anonymous Proxy Servers
High Anonymity Proxy Server (Level 1)
High anonymity proxy servers anonymize your originating IP address and don’t identify themselves to web domains as proxies. These are ideal for users who need a high level of privacy and security. High anonymity proxies are often used by individuals who need to protect sensitive information, such as journalists, activists, and those living in countries with strict internet censorship.
Anonymous Proxy Server (Level 2)
Anonymous proxy servers change your destination IP address to that of the proxy server but will also identify themselves as proxies to the web domain. Another type of anonymous proxy is a distorting proxy, which conceals a user's real IP address and sends a false IP address for the user's location, making them appear to be in a different location than where they actually are. These proxies offer a balance between anonymity and performance, making them suitable for general use.
Transparent Proxy Server (Level 3)
Transparent proxy servers don’t anonymize the originating IP address of a user and will show exactly where a traffic request is coming from. These proxies are often used in public Wi-Fi networks and corporate settings for monitoring and filtering content. Transparent proxies are also used in content delivery networks (CDNs) to optimize the delivery of web content by caching it closer to the end user.
How Proxy Servers Work with Protocols
HTTP
HTTP proxies use the unsecured HTTP protocol to route user traffic requests/downloads. These proxies are easy to set up but do not provide encryption, making them less secure for sensitive information. They are typically used for non-sensitive browsing activities, such as accessing public websites or retrieving online content.
HTTPS
HTTPS proxies use the HTTPS protocol to encrypt your traffic and allow you to connect to HTTPS web domains protected by SSL certificates. This encryption ensures that your data remains secure during transmission. HTTPS proxies are essential for activities that involve sensitive information, such as online banking, shopping, and accessing secure websites.
SOCKS
SOCKS proxies allow the transfer of data and traffic compatible with the SOCKS5 protocol. They are versatile and can handle various types of traffic, including web, email, and peer-to-peer. SOCKS proxies are often used for applications that require a high level of security and flexibility, such as gaming, video streaming, and file sharing.
DNS
DNS proxies are common online and work by forwarding a DNS request from the user to a DNS-based web domain or server. They are often used to bypass geographic restrictions and access blocked content. DNS proxies can also improve the speed and reliability of DNS resolution, reducing latency and improving overall internet performance.
Smart DNS
Smart DNS proxies allow you to spoof your geolocation by only diverting one part of your internet traffic, specifically, DNS requests. This makes them ideal for streaming services that restrict content based on location. Smart DNS proxies offer a quick and efficient way to access geo-restricted content without impacting the overall speed of your internet connection.
CGI
CGI-based proxies are a type of web proxy server that allows you to use the proxy’s features through your browser or internet client. They are typically used for simple tasks like bypassing IP restrictions. CGI proxies are often used in educational and corporate environments to provide easy access to proxy services without requiring complex configurations.
Benefits of Using a Proxy Server
Control internet access
Proxy servers can monitor users’ internet access and block sites with content deemed unacceptable. This is particularly useful in corporate and educational environments where access to certain websites needs to be restricted. By controlling internet access, organizations can improve productivity, reduce the risk of malware infections, and enforce acceptable use policies.
Improve privacy
Web proxies change your IP address and other identifying data, keeping your personal information private. Anonymous proxies and web proxies have their own IP address, which they use to conceal a user's real IP address and provide anonymity. This is beneficial for users who want to protect their identity online. By masking your IP address, proxies can help prevent targeted advertising, reduce the risk of online tracking, and enhance your overall privacy.
Access blocked sites
You can use a proxy server to access blocked websites, even if your employer or school blocks certain sites. This is a common practice for bypassing geographic restrictions and accessing content that is otherwise unavailable in certain regions. By using a proxy server, you can gain access to a wide range of online content, including social media platforms, streaming services, and news websites.
Improve speed and save bandwidth
Web proxies cache web pages, saving the most recent copy of frequently visited websites. Datacenter proxies can be used to create artificial IP addresses, providing anonymity and faster speeds, although they are less reliable than residential proxies. This caching reduces load times and conserves bandwidth. By caching web content, proxies can reduce the load on your internet connection, improve the performance of frequently accessed websites, and minimize the impact of network congestion.
Risks of Using a Proxy Server
Risks associated with using a free proxy server
Free proxy servers often raise security concerns, as they may sell their users’ bandwidth or collect sensitive data. These servers might lack proper security measures, making your data vulnerable to interception and misuse. Free proxies are also more likely to display intrusive ads, inject malware, and track your browsing activities, posing significant risks to your privacy and security.
Logging your browser history
Many proxy servers save your unencrypted IP address and web request information, which may be sold to another vendor. This poses a risk to your privacy, as your browsing habits can be tracked and analyzed. To mitigate this risk, it is important to use reputable proxy services that do not log your browsing activities and have a clear privacy policy.
Spam and virus attacks
You may see more banners and ads when you connect to a site through a proxy server. These ads can be intrusive and sometimes lead to malicious websites that distribute malware and viruses. To protect yourself from spam and virus attacks, use a proxy server with robust security features, including ad-blocking and malware protection.
Identity theft
Although a web proxy keeps your IP address and data private, the proxy vendor has access to everything. Understanding proxy server settings is crucial to ensure data security and prevent identity theft, especially when using unencrypted proxies. Always use reputable proxy services to mitigate these risks. Look for proxies that use encryption, have a no-logs policy, and offer additional security features, such as multi-factor authentication and IP whitelisting.
Proxy Server vs. VPN
Key differences between a proxy server and a VPN
Proxy servers and VPNs both act as intermediaries between the user and a website, but they operate differently and serve distinct purposes.
Proxy Servers:
- Anonymity and Performance: Proxy servers, especially residential proxies, route your internet traffic through an intermediary server, masking your IP address with one from a residential IP pool. This makes it appear as though your traffic is coming from a legitimate residential location, enhancing anonymity and reducing the chances of being flagged by websites.
- Selective Traffic Routing: Proxies can be configured to handle specific types of traffic or connections. For example, you can use a proxy for web browsing while other traffic goes directly to the internet.
- Caching and Bandwidth Savings: Proxy servers can cache web content, which can reduce load times and save bandwidth for frequently accessed websites.
VPNs:
- Full Encryption: VPNs route all your internet traffic through an encrypted tunnel, providing a high level of security and privacy. This is particularly useful for protecting sensitive information on public Wi-Fi networks.
- Complete Traffic Protection: Unlike proxies, which typically handle only specific types of traffic, VPNs encrypt all data coming from your device, ensuring comprehensive protection against eavesdropping and data interception.
- Consistent Performance: While VPNs provide robust security, they can sometimes slow down your internet connection due to the encryption overhead. However, high-quality VPN services minimize this impact.
In summary, while both proxies and VPNs offer privacy and security benefits, they cater to different needs. Proxies, particularly residential proxies, are excellent for specific tasks requiring high anonymity and reliable IP addresses. In contrast, VPNs provide comprehensive encryption and are suitable for users seeking complete privacy across all their internet activities.
Here's a quick comparison table between proxies and VPNs:
<table class="GeneratedTable">
<thead>
<tr>
<th>Category</th>
<th>VPN</th>
<th>Proxy</th>
</tr>
</thead>
<tbody>
<tr>
<td>Functionality</td>
<td>Encrypts entire internet connection</td>
<td>Intermediary for specific applications</td>
</tr>
<tr>
<td>Security and Privacy</td>
<td>High-level encryption, hides IP, bypasses geo-blocks</td>
<td>Varies: Non-SSL less secure, SOCKS5 balances speed and security, hides from ISPs</td>
</tr>
<tr>
<td>Setup and Configuration</td>
<td>Complex: install client, select server and protocol</td>
<td>Easier: input server address and port</td>
</tr>
<tr>
<td>Internet Performance</td>
<td>May slow down due to encryption and server distance</td>
<td>Generally faster without encryption overhead</td>
</tr>
<tr>
<td>Compatibility</td>
<td>Wide range of devices and apps, some need extra setup</td>
<td>Works with devices/apps supporting proxy settings, often limited to one app/browser at a time</td>
</tr>
<tr>
<td>Cookies and Trackers</td>
<td>Blocks/deletes cookies and trackers, includes ad blockers</td>
<td>May block cookies but less effective against advanced trackers</td>
</tr>
</tbody>
</table>
Proxy Servers Use Cases
Proxy servers are used in various scenarios, providing benefits across different sectors and individual needs. Here are some key applications:
- Business and Institutional Use:
- Enhance Productivity and Security: Optimize internet usage, block access to harmful websites, and protect company or institutional networks from cyber threats.
- Control and Monitor Usage: Manage and restrict access to non-essential or inappropriate content, ensuring responsible and productive internet use.
- Individual Use:
- Bypass Restrictions and Access Content: Reach region-locked content and streaming services, and access geo-blocked websites.
- Private Browsing: Enhance privacy by masking your IP address, allowing for anonymous browsing.
- Research and Data Collection:
- Anonymously Gather Data: Collect information without revealing your IP address.
- Web Scraping: Automate data extraction for SEO and market analysis.
- Content Delivery and Performance:
- Improve Load Times: Cache frequently accessed websites to speed up load times and save bandwidth.
- Efficient Distribution: Manage and distribute content effectively across different regions.
- Enhanced Security:
- Additional Security Layer: Protect sensitive online activities by masking your IP address.
- Reduce DDoS Risks: Mitigate the risk of DDoS attacks by hiding true IP addresses.
- Social Media Management:
- Manage Multiple Accounts: Handle multiple social media profiles without getting flagged.
- Conduct Analysis: Perform detailed social media analysis and engagement anonymously.
These applications demonstrate the versatility of proxy servers in enhancing security, privacy, and efficiency across various activities and industries.
Choosing the Right Proxy Server for Your Needs
Selecting the right proxy server depends on your specific needs. For basic browsing and anonymity, an anonymous proxy server might suffice. However, if you need higher security and speed, consider using a VPN or a high anonymity proxy server. Consider factors such as the proxy’s location, the level of anonymity it provides, its speed and reliability, and the reputation of the proxy service provider.
Massive offers high-quality residential proxies that provide superior performance, security, and anonymity for various online activities. These proxies are 100% ethically sourced and are ideal for tasks such as international keyword research, local market analysis, and managing multiple social media accounts. With Massive's residential proxies, you can ensure a seamless, secure, and efficient online experience.
Final Thoughts: Do I Need a Proxy Server?
Whether you need a proxy server depends on your specific online activities and concerns, but understanding how proxy servers work and choosing the right solution is important for protecting your privacy and security. Consider your needs, evaluate the options available, and select a proxy server that aligns with your requirements for a safer and more efficient online experience. By staying informed about the latest developments in proxy technology and best practices, you can maximize the benefits of using a proxy server while minimizing potential risks.
Customer reviews
Frequently Asked Question
+
+
+
+
+
+
+
+
+
+
Discover your ideal proxy
Loading...
















